This is a paid feature depending on your contract. If you don't see the menu and want to use this feature, please contact your sales representative or the Sansan Support Center.
This page describes how to use IdP (identity provider) settings for SAML authentication. To set up this feature, you need to add a new IdP setting in advance (Read this for how to do the setup). Sansan can be integrated with various IdPs using external authentication with the SAML 2.0 protocol. This feature lets users log in to Sansan using IdP-managed IDs, passwords, etc.
Contents
- Details
- Setting units
- Company-wide settings
- Contract-specific settings
- User-specific settings
- Logging in after enabling SAML authentication
- If SAML authentication fails and you can't log in
- Setting up SAML authentication
Details
- You cannot use the Web App for normal login and Mobile App version for SAML authentication.
- SAML authentication links authentication information from the IdP to Sansan for login. There is no function to automatically reflect user additions, changes, or deletions on the IdP in Sansan.
- Two-factor authentication cannot be used once SAML authentication is enabled.
- Users with SAML authentication enabled will be forced to log out of the Mobile App. Please consider informing users of the change in authentication method and then adjusting the implementation time accordingly. Note that the Web App does not force logout when SAML authentication is activated.
- IdP-issued certificates must be renewed before they expire. Please manage them proactively.
- The operation test in the procedure is for the Web App only. Sign up for a free trial separately to test the Mobile App. Contact the Sansan Support Center to find out how to sign up.
Setting units
Settings can be divided into three units.
• Settings (company-wide): Affect the entire company
• Settings (contract-specific): For each contract
• Settings (user-specific): For individual users within a contract
If all settings are made for each unit, the order of priority is (1) user-specific, (2) contract-specific, and (3) company-wide.
Company-wide settings
Settings (company-wide) will be applied to the entire company, regardless of the contract’s scope.
Go to Admin settings → Security Settings → SAML Authentication → Settings (company-wide).
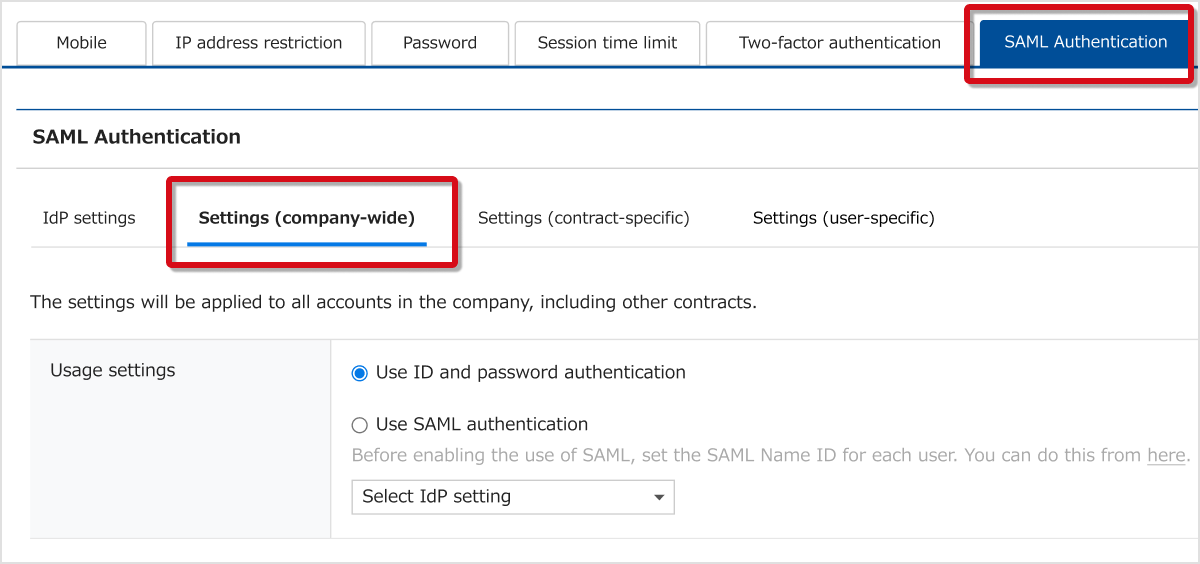
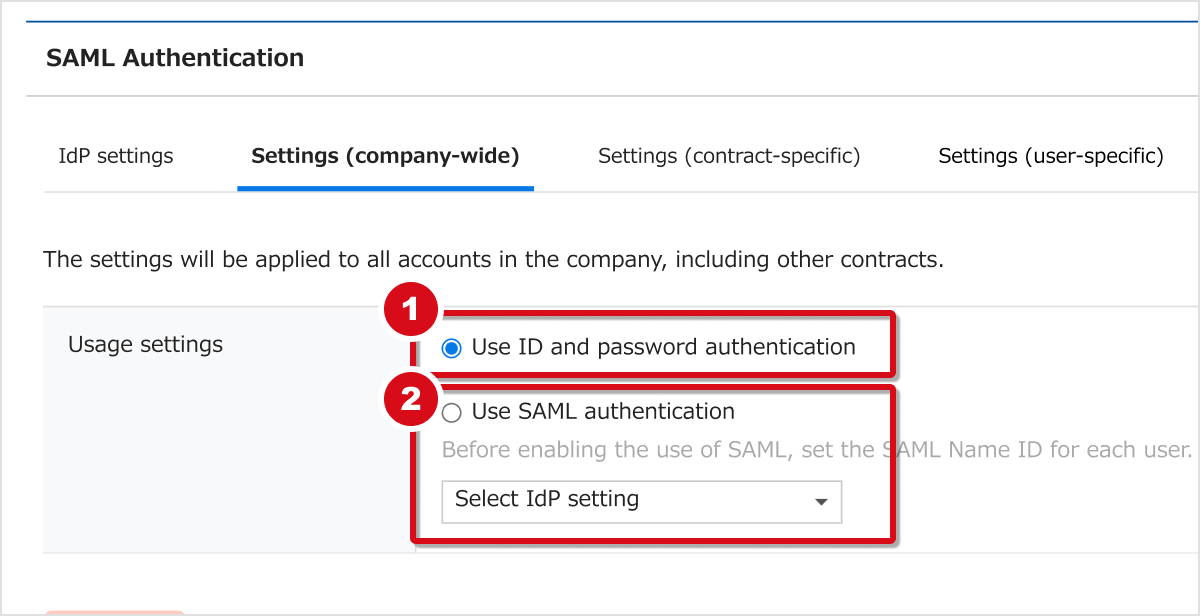
Use ID and password authentication
The default value is set here.
Use SAML authentication
Select the IdP setting you'll use. Pre-added IdP settings will be shown as choices. Note that users who haven't been assigned a SAML Name ID will not be able to log in.
- IdP must be set up in advance. Read this for how to do the setup.
- SAML authentication requires the setting of a SAML Name ID for each user. Read this for how to change user information.
Contract-specific settings
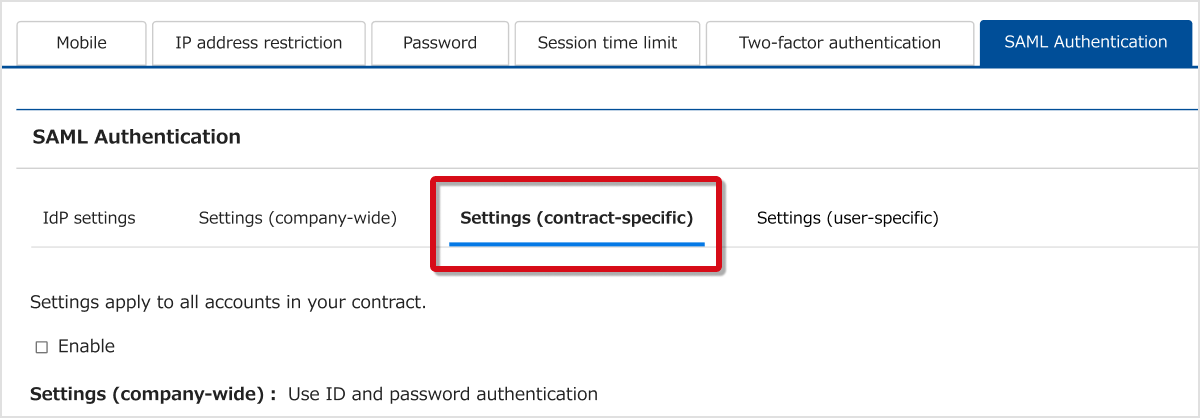
These settings affect only within the scope of the contract managed that the operator manages.
When enabled, these settings have priority over company-wide settings. All users who can access Admin settings → Manage users are affected.
Go to Admin settings → Security Settings → SAML Authentication → Settings (contract-specific).
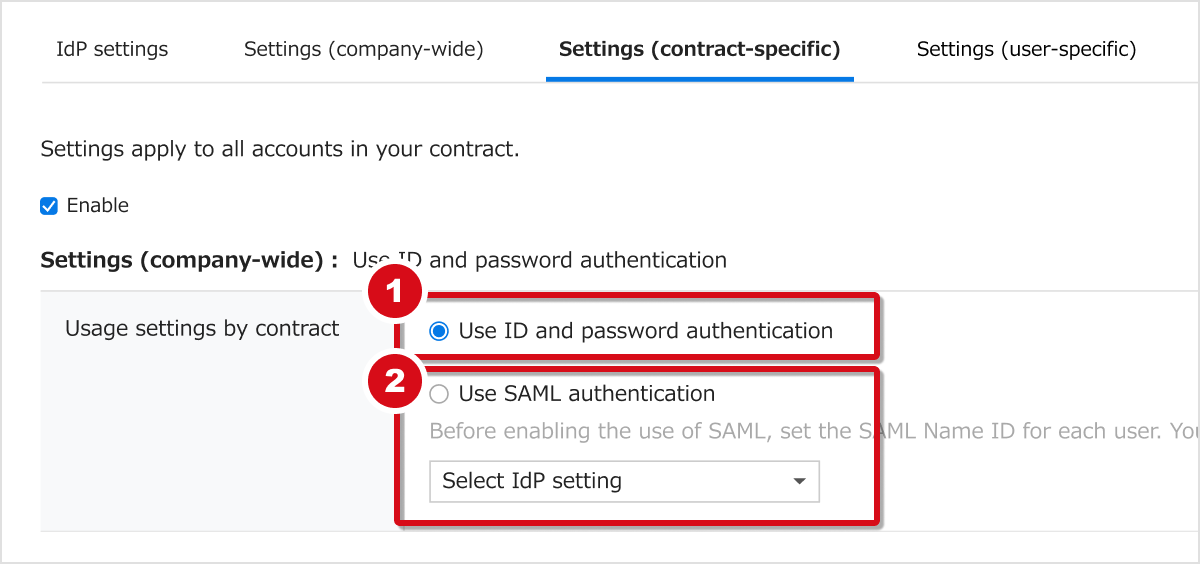
Use ID and password authentication
The default value is set here.
Use SAML authentication
Select the IdP setting you'll use. Note that users who haven't been assigned a SAML Name ID will not be able to log in.
- IdP must be set up in advance. Read this for how to do the setup.
- SAML authentication requires the setting of a SAML Name ID for each user. Read this for how to change user information.
User-specific settings
Go to Admin settings → Security Settings → ① SAML Authentication → ② Settings (user-specific) → ③ Add.
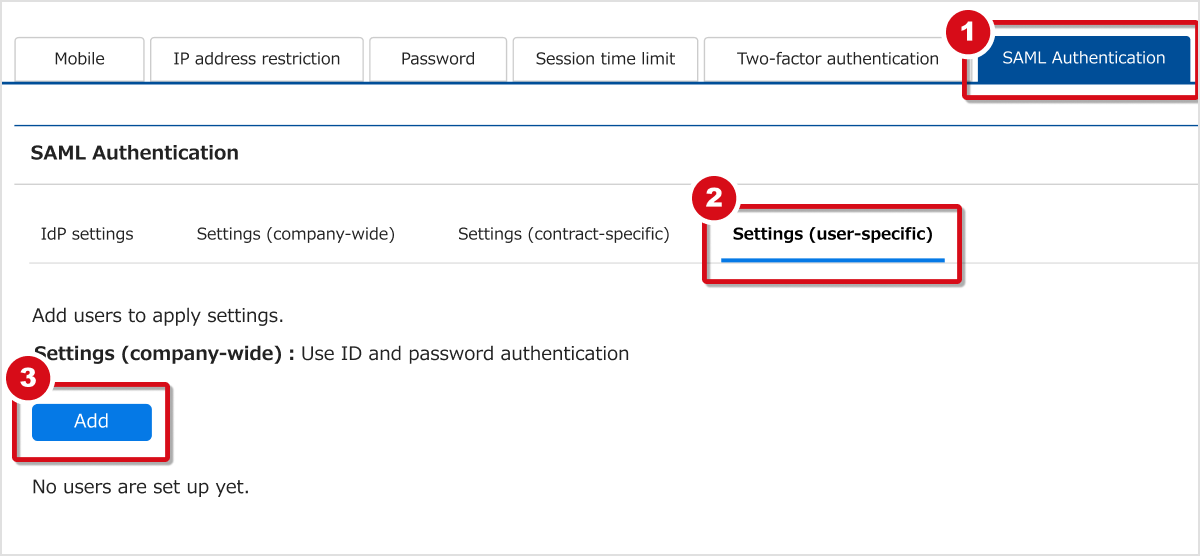
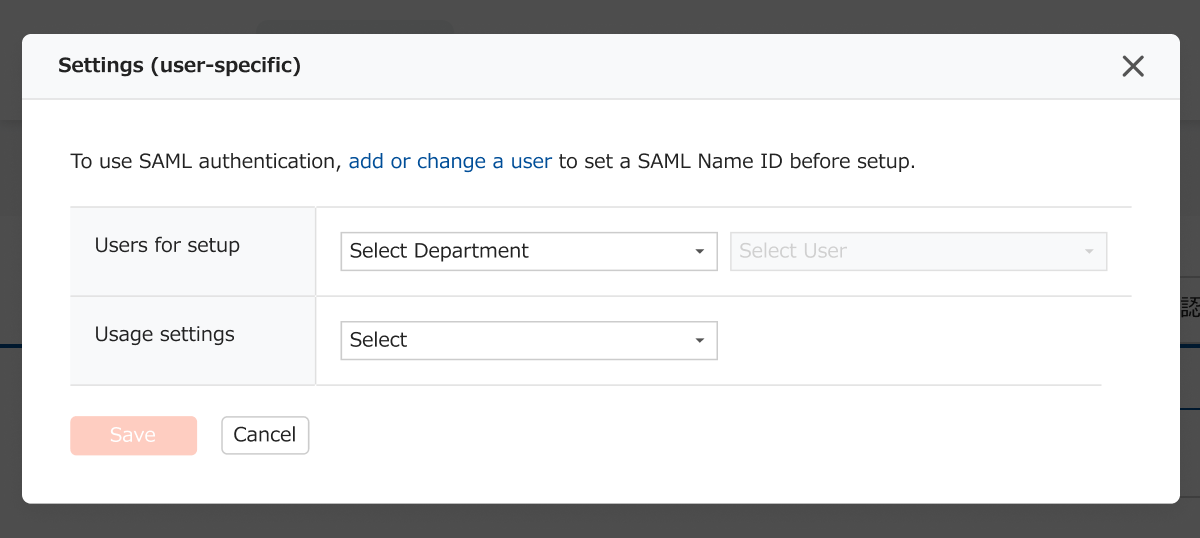
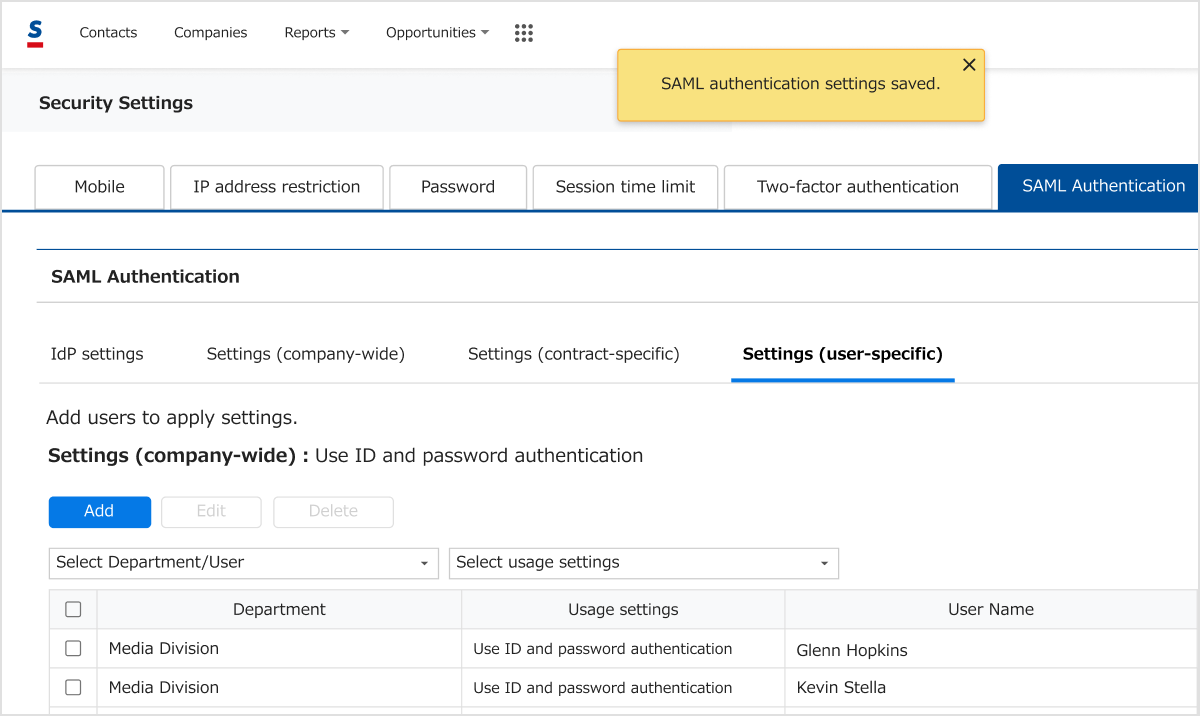
Go to Users for setup, Usage Settings, and save. The list will show users to whom the settings were applied.
Note that users who haven't been assigned a SAML Name ID will not be able to log in.
- IdP must be set up in advance. Read this for how to do the setup.
- SAML authentication requires the setting of a SAML Name ID for each user. Read this for how to change user information.
Logging in after enabling SAML authentication
Enabling SAML authentication will change the login method. Be sure to inform your users beforehand.
How to login
Web App
On the regular login screen, click “Log in with SSO". On the next screen, enter the email registered with Sansan (①) and click "Continue" (②). It will redirect to the authentication screen of the IdP that was set up. Log in with the IdP-managed user ID and password.
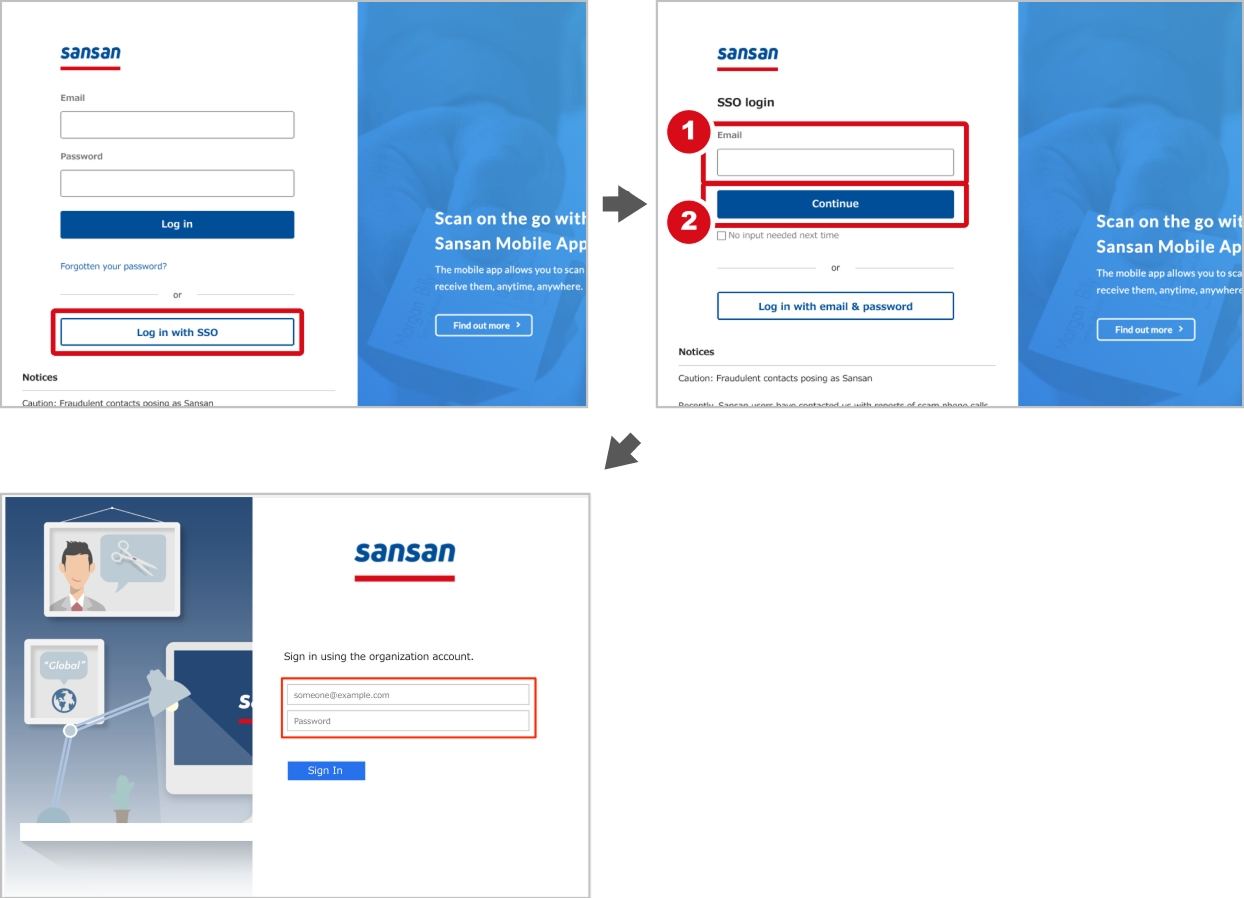
Mobile App
On the regular login screen, tap "Log in with SSO". On the next screen, enter the email address registered with Sansan (①) and tap "Continue" (②). It will redirect to the authentication screen of the IdP that was set up. Log in with the IdP-managed user ID and password.
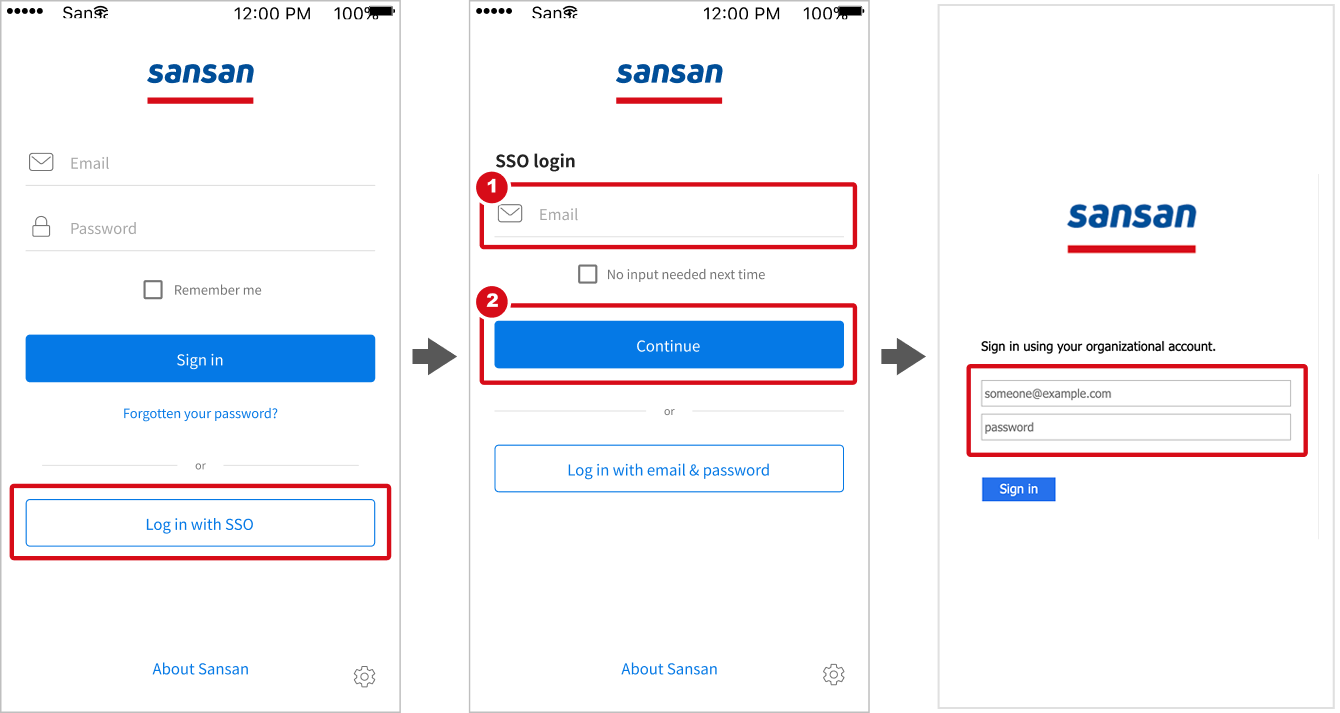
*This image is an example, and what you see may vary depending on the IdP used.
If SAML authentication fails and you can't log in
See this page for how to log in to the IdP and perform the recovery process without screen transitions.
Setting up SAML authentication
Go here to see how to set up SAML authentication.