This feature is a paid option. Please contact our sales team or Sansan Support Center if you would like to use it.
Sansan can work with various IdPs (identity providers) by using external authentication via the SAML 2.0 protocol. This enables login to Sansan with IDs and passwords managed by the IdP.
Contents
Key Points
- You cannot use the Web App for normal login and the Mobile App for SAML authentication. Certificates issued by IdP must be renewed before they expire. Be sure to actively manage them.
- SAML authentication integrates authentication information on the IdP with Sansan for login. There is no function to automatically reflect user additions, changes, and deletions on the IdP in Sansan.
- When SAML authentication is enabled, two-factor authentication (2FA) cannot be used.
- Users with SAML authentication enabled will be forcibly logged out of the Mobile App. Consider informing your users of the change in authentication method, and making the change at a suitable time. Note that the Web App does not force a logout because of SAML authentication activation.
- IdP-issued certificates must be renewed before they expire. Please be sure to keep track of them.
- After completing the operational test in the procedures, the IdP setting can be selected as available for authentication.
- The operational test in the procedures is for the Web App only. For testing the Mobile App, try logging in with SAML authentication enabled only for the user who will perform the verification as in "Settings (user-specific)".
Adding a new IdP setting
Preparation
- A SAML Name ID must be set for each user. See here for how to change user information.
- System administrator privileges are required to enable SAML authentication.
Add a new setting from "Admin settings" > "Security settings" > "SAML Authentication" > "Add new IdP setting".

1.For the IdP
Set a name for your IdP.

Choose the IdP from the "Select IdP" pulldown. If it's not visible, choose "Other". Read about selectable IdPs.

When choosing "Other", select "Single" or "Multiple" Entity ID based on the specifications of the IdP to be used. If you have any questions, please contact the IdP provider.

*If you don't choose "Other", the entity ID suitable for the selected IdP will be automatically selected.
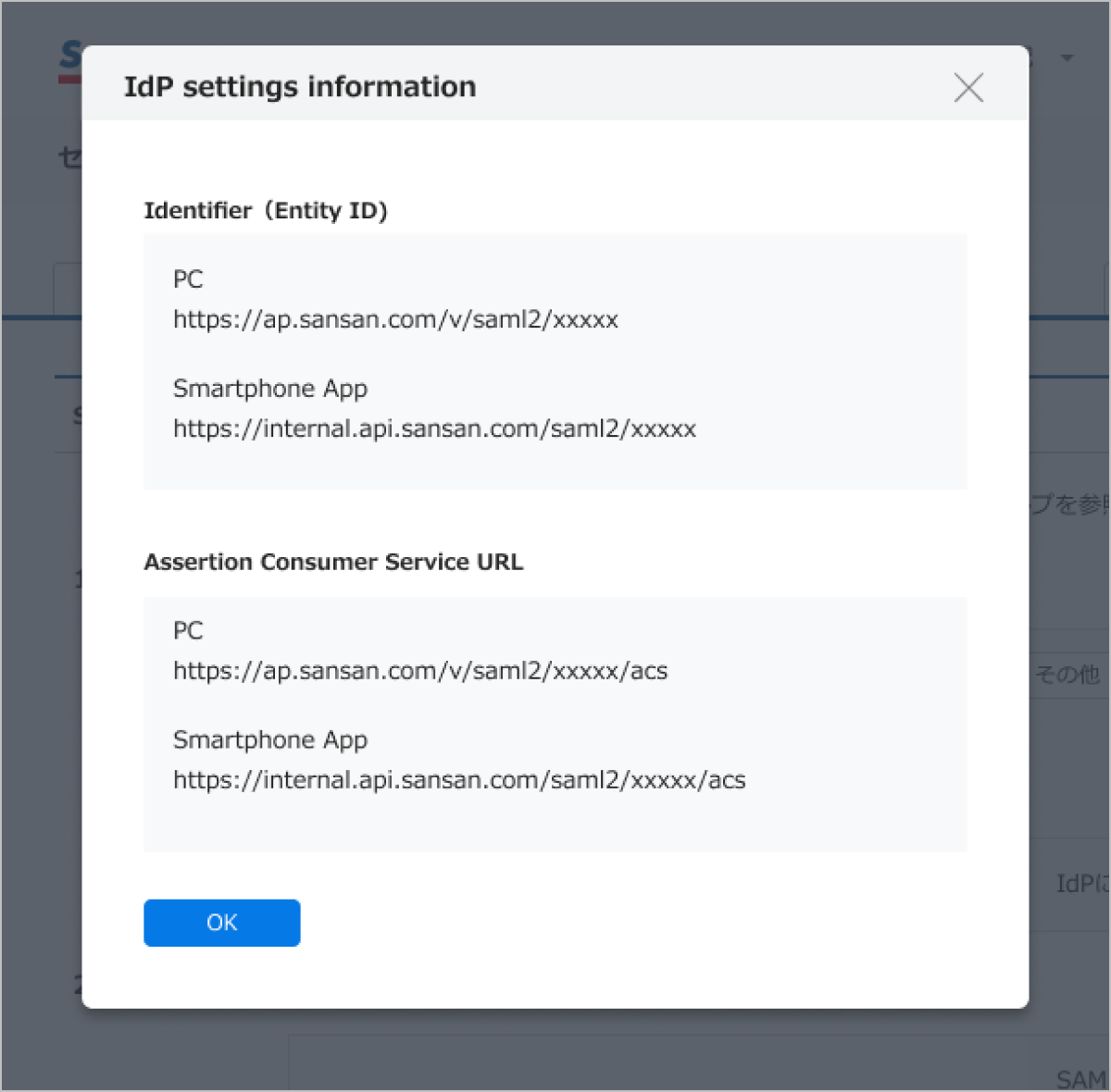
Choose to show "IdP settings information", make a note of the displayed content, and enter it for the IdP.

- For single Entity IDs
*Example

- For multiple entity IDs
*Example
2.For Sansan
To use MDM, check "Use".
*If you use Microsoft Intune, etc. device management or access control, place a check here.
Default browser for iOS devices
If you choose to use MDM, you’ll see an option for the default browser on the iOS device.
The default browser will be used to exchange certificates from MDM to IdP. To use another browser, you need to change to ① use a browser other than Safari before you can log in.
If you’re not using Safari, click the ② Back to Sansan button shown after authentication, and return to the app.


Enter the IdP settings.

Check with your IdP provider if you are unsure what to enter. Be sure to enter the settings exactly and without adding extra spaces.
Upload the SAML signing certificate.

The extension will be .cer.
Enter the following settings for IdP side for the signature on the SAML response.
- Digest algorithm: either sha-256 or sha-512
- Signature algorithm: either rsa-sha-256 or rsa-sha-512
3.Verifying settings
"Start" the test.

Clicking "Start" will automatically redirect to the IdP login screen. Enter your IdP ID and password to authenticate.

*Example
If there are no problems with the test, you're good to go.
Please note that saving does not activate the settings.

An IdP setting will be added.

Status shown in the list
The status depends on the IdP configuration when it is saved. Details are as follows.
| Status | Description |
|---|---|
| Setup not completed | Setup not completed |
| Available | The IdP configuration has been completed up to the operational test and is ready for use. |
Testing errors
If the test results in an error, the actual SAML response will be displayed on the screen along with an error message instructing you how to modify the Sansan or IdP settings accordingly.
| Error | Issues that may arise |
|---|---|
| IdP identification name is incorrect. | If the IdP name set on the Sansan screen does not match that of the actual SAML response, be sure to correct one of them so they match. |
| SAML certificate is incorrect. | If there is a problem with the certificate, reissue it and try again. |
| SAML Name ID is not registered correctly. | The SAML Name ID set in Sansan's user management screen does not match the Name ID in the actual SAML response. Correct one of them so they match. Cached information may also remain. This can be resolved by deleting the cache or using incognito mode in your browser. |
| No value has been entered for Audience. | For the IdP Audience value set the identifier as the entity ID. |
| An unsupported signature algorithm has been specified. | Please specify RSA-SHA-256 or RSA-SHA-512. |
| 403 or 404 errors are shown (error messages, SAML responses are not shown) | In the Sansan SAML authentication settings screen, make sure the information set for the IdP is correct. Also, check that the settings and certificates on the IdP that are set in Sansan are correct. The response URL differs between the Sansan web and app versions. If multiple response URLs can’t be set for an IdP, please contact the respective IdP for the registration method. |
Selectable IdPs
IdPs for which SAML authentication has been confirmed to work are as follows.
| IdP | Entity ID |
|---|---|
| Active Directory Federation Services | Single |
| Auth0 | Single |
| Microsoft Entra ID(Formerly Azure Active Directory) | Single |
| CloudGate UNO | Single |
| Google Workspace | Multiple |
| HENNGE One | Multiple |
| Okta | Single |
| OneLogin | Single |
If you are unable to login with SAML authentication
When a user cannot log in from the IdP (such as when SAML authentication is mistakenly set), the system admin can log in without transitioning to the IdP and recover their account.
Steps
- Log in with this URL. If you've forgotten your password, you can reset it from here.
- Reset SAML authentication settings or re-upload the certificate.
FAQ
Q: What can I do if I want to use Microsoft Intune and log in using device certificates, etc.?
A: In Sansan’s IdP settings check the box to use MDM. Device certificate authentication will be enabled, and Safari for iPhone and Google Chrome for Android will be launched. Check the relevant box if you want to use a default browser other than Safari.
Q: What can I do if I get the following message? “Login failed. The information does not match what's registered in Sansan or service may be restricted. SSO may also not be configured. Please contact your system admin with any questions.”
A: Please check for the following likely causes.
1) The email address is incorrect.
Go to “Admin Settings” “Manage users” and check the user’s email address.
2) SSO (single sign-on) settings are not entered or are incomplete. See this page for more details.
If you can’t log in despite setting up a SAML Name ID, it's possible that the SAML Name ID* registered in your Sansan user information and the user information registered in your IdP do not match. Be sure they match exactly, including upper-case/lower-case letters.
*The SAML Name ID can be checked from “Admin Settings” “Manage users”.
3) The user is not registered.
Go to “Admin Settings” “Manage users” and check the user’s email address. If there is no user registered for that email address, add a user (details here).
4) The admin suspended the account.
Go to “Admin Settings” “Manage users”, and check the account status of the relevant user. If the account is “Inactive”, change it to “Active”.
Q: Can I log in from the IdP screen (IdP-Initiated)?
A: Sansan only supports SP-Initiated* SAML authentication.
*After accessing Sansan, access your IdP, and connect to Sansan after authenticating with the IdP.
Some IdPs have reported operation with IdP-Initiated, but we do not guarantee this operation. Please use the service at your own risk.
Q: Do you provide metadata about configuration information in an XML file?
A: No, we do not. Please refer to the IdP settings information on the Sansan IdP settings page for information to be set for the IdP.
Q: Is it OK to change the extension of the SAML signature certificate downloaded by the IdP to .cer?
A: Yes, the extension of the SAML signature certificate you set up with Sansan must be .cer.
Q: Can SAML authentication and two-factor authentication be used together?
A: No, they cannot. When SAML authentication is set up, authentication takes place with the IdP. if the IdP has two-factor authentication set up, please use that.
Q: Can SAML authentication and device restrictions be used together?
A: Yes, they can.
Q: Can SAML authentication and IP address restriction be used together?
A: Yes, they can. If access is made from an unauthorized IP address, an error will occur after authentication.
IdP setup manuals
These are configuration manuals for each IdP (external links). Please contact each IdP for more information on the contents.
Microsoft Entra ID(Formerly Azure Active Directory)
https://docs.microsoft.com/ja-jp/azure/active-directory/saas-apps/sansan-tutorial
Cloud Gate UNO
https://cg-support.isr.co.jp/hc/ja/articles/900001151446
HENNGE One
https://teachme.jp/35563/manuals/25516985
GMOトラスト・ログイン
https://support.trustlogin.com/hc/ja/articles/900004762866